This guide presents a production-grade architecture for AI-powered compliance monitoring that analyzes 100% of communications in real-time. Key components:
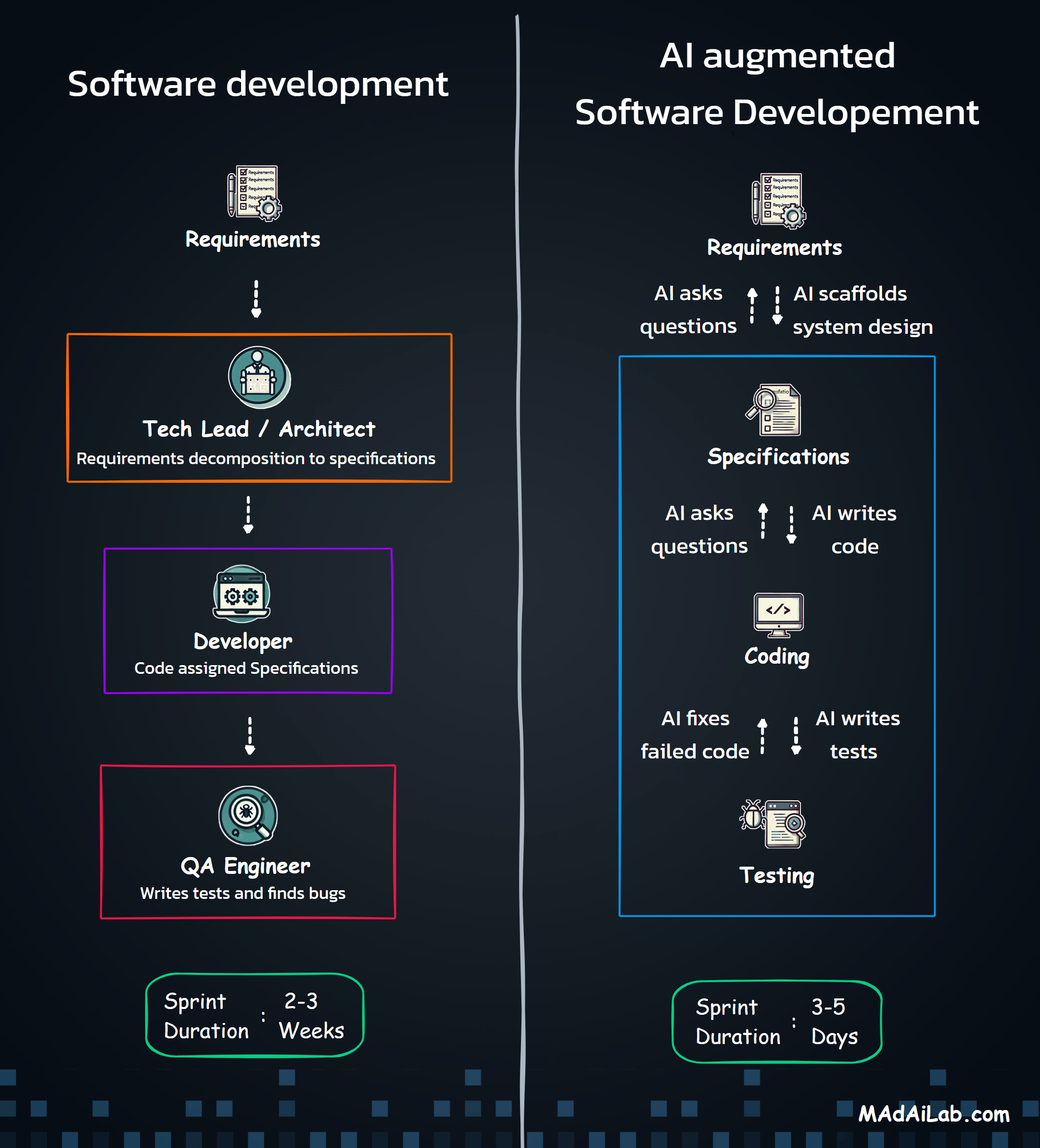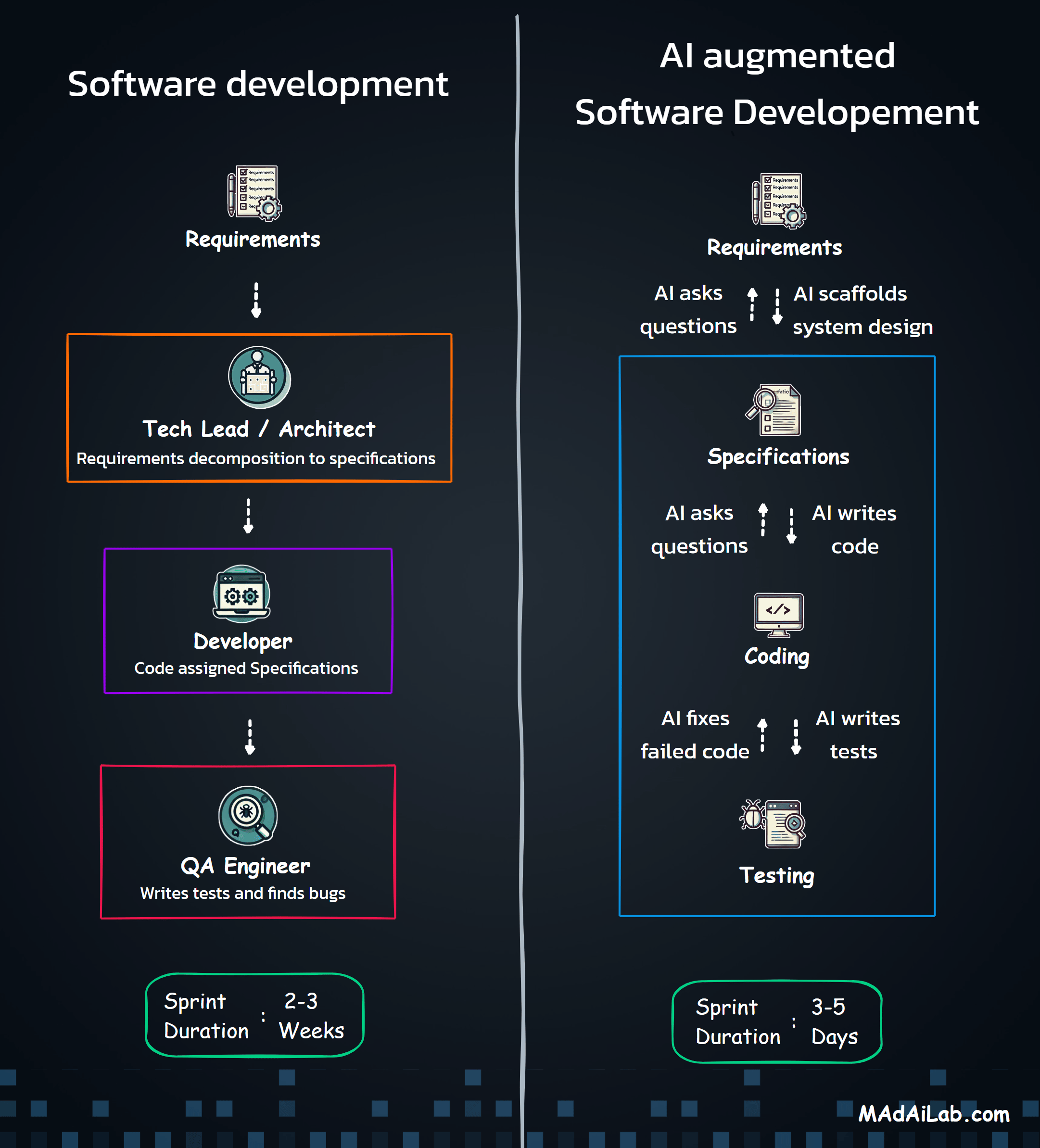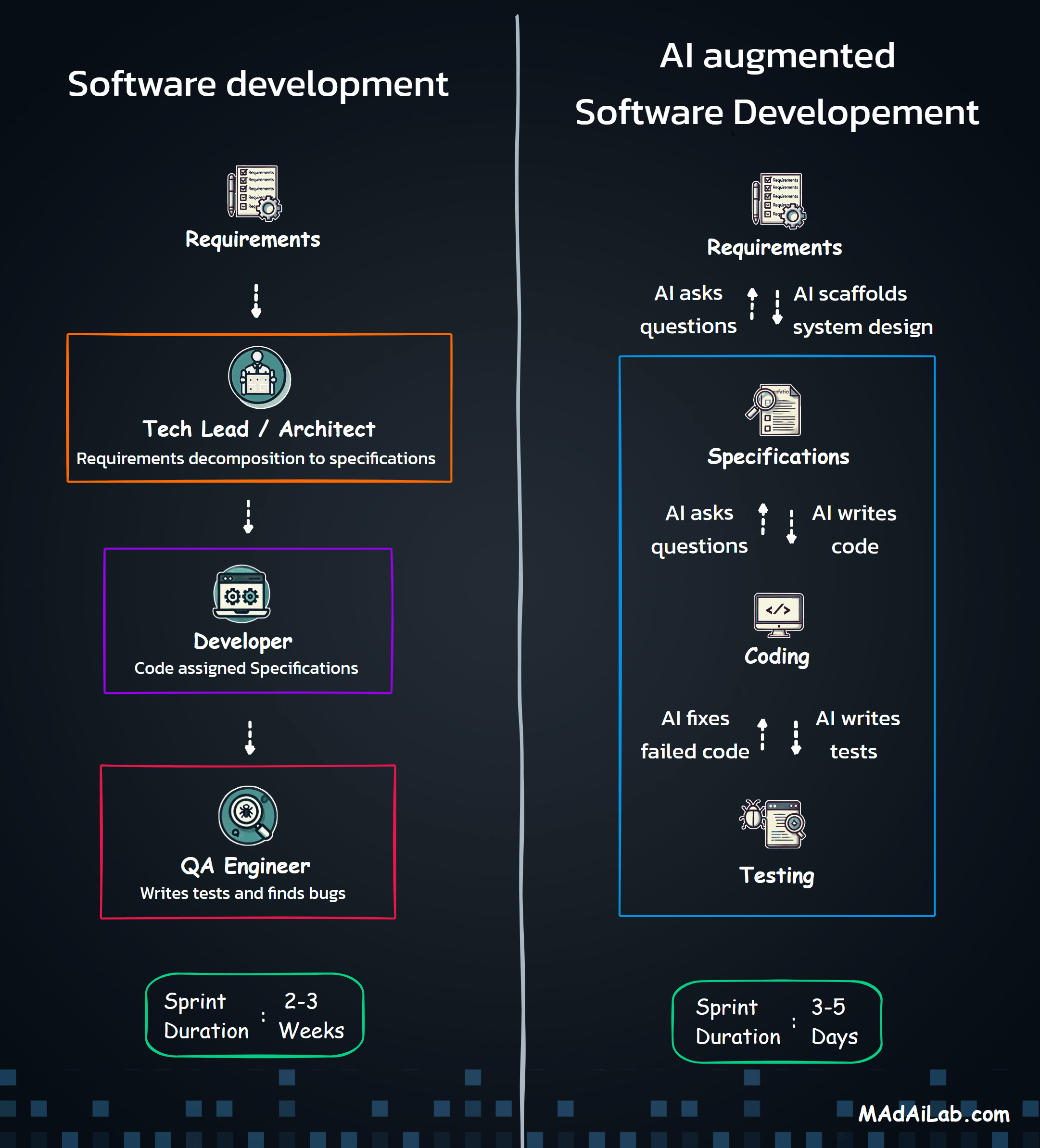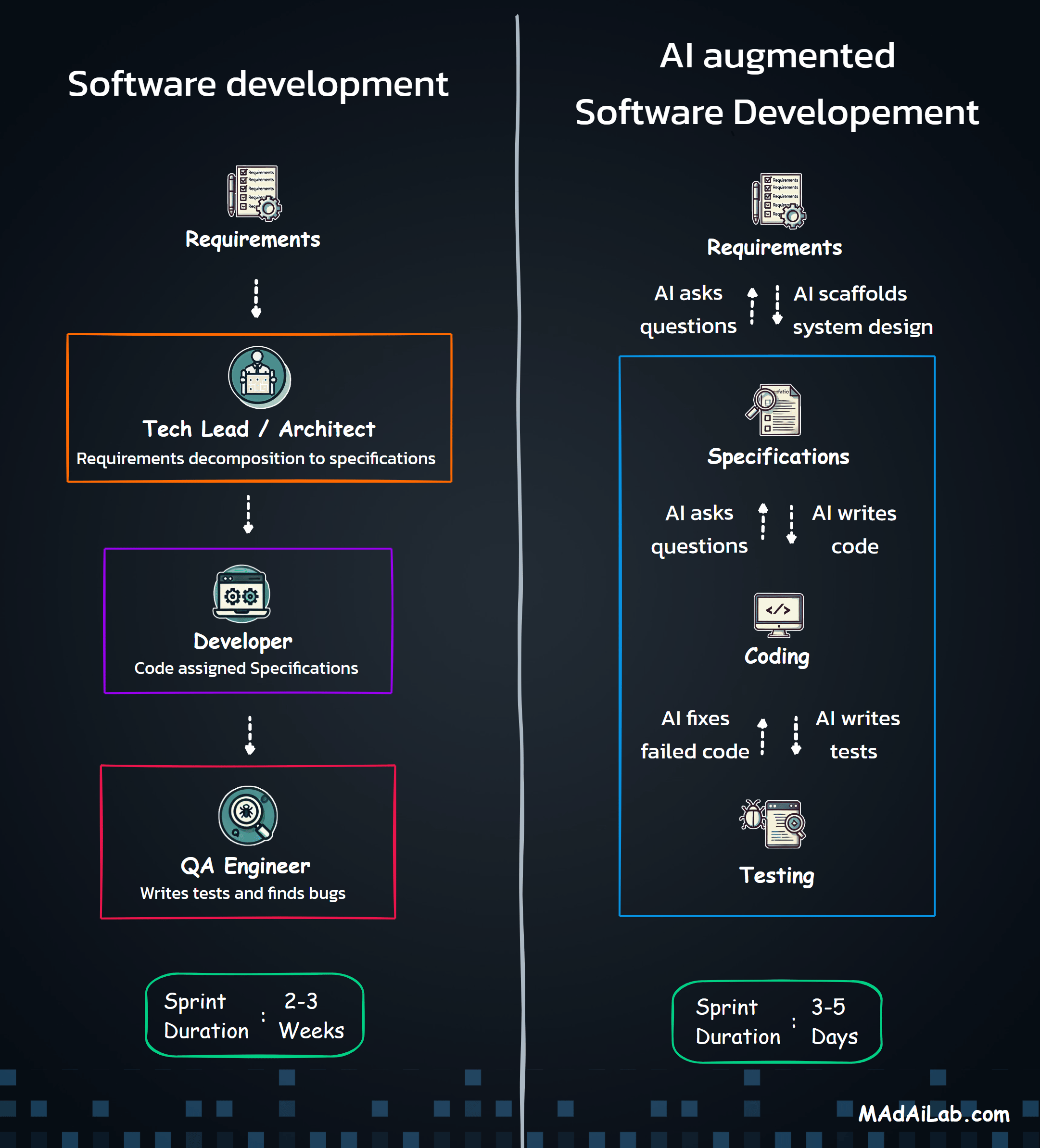
The architecture is technology-agnostic, applicable across workflow automation tools, traditional frameworks, or serverless platforms. It transforms compliance from reactive sampling (1-5% coverage) to proactive monitoring (100% coverage) with real-time detection.
A single compliance violation can cost millions in fines and permanent reputational damage. Yet traditional audit approaches examine only 1-5% of organizational communications. This guide presents a production-grade architecture for AI-powered compliance monitoring that analyzes 100% of communications in real-time, transforming compliance from reactive auditing to proactive risk management
While we reference specific technologies as examples, the architectural patterns apply across platforms—workflow automation tools, traditional frameworks, or cloud-native architectures.
Modern organizations face an impossible challenge:
Intelligent automation transforms the game:
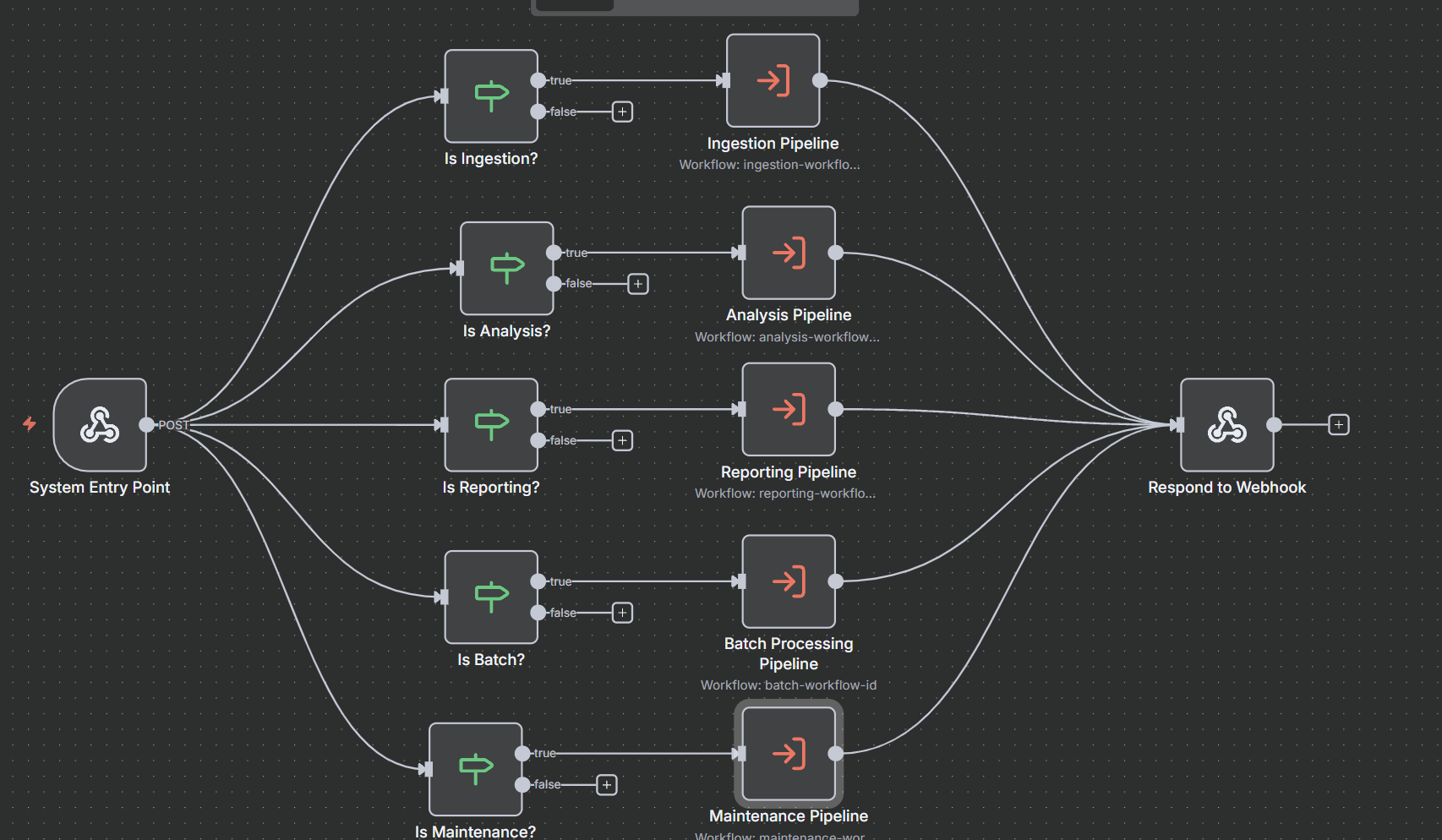
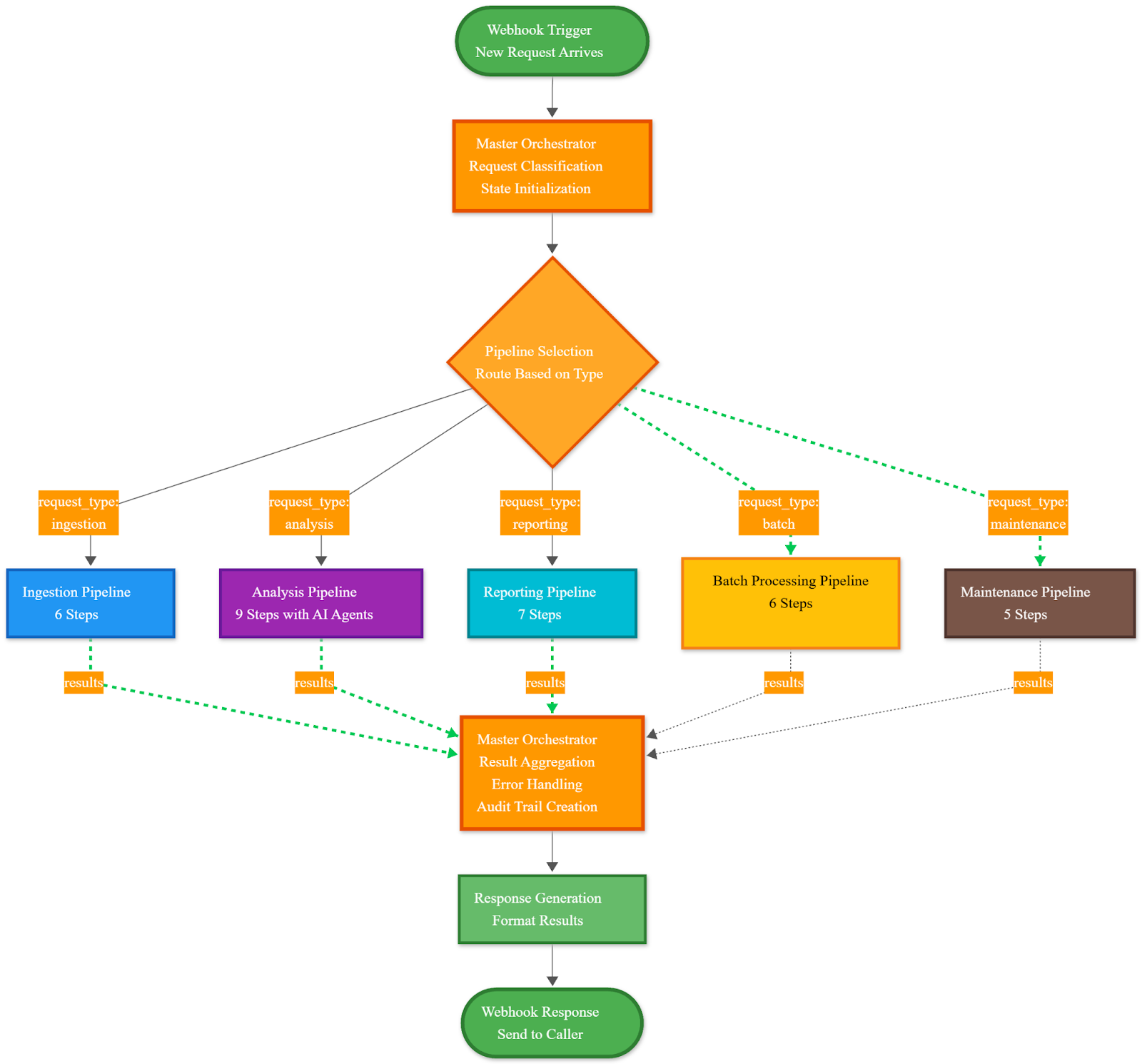
Building compliance isn't one process—it's coordinating dozens of specialized operations. The Master Orchestrator acts as the system's nervous system, receiving requests, routing to appropriate pipelines, coordinating sub-processes, and managing state across complex operations.
Key Principle: Like a conductor coordinating musicians, the orchestrator ensures specialized processes work in harmony rather than chaos.
1. Ingestion Pipeline - Data onboarding and normalization
2. Analysis Pipeline - AI-powered compliance analysis (the intelligence core)
3. Reporting Pipeline - Strategic intelligence
4. Batch Processing Pipeline - Historical analysis and bulk operations
5. Maintenance Pipeline - System health and optimization
Critical Pattern: The orchestrator maintains context, implements graceful degradation, tracks metrics, and enforces consistent error handling across all pipelines.
A single AI model cannot excel at rule-based compliance checking, statistical anomaly detection, AND strategic reporting simultaneously. The multi-agent approach leverages specialized models for specialized tasks.
Pattern: Agent coordination via state machine workflow that initializes shared context, routes documents through specialized agents, manages conditional logic, aggregates findings, and calculates composite risk scores
Specialty: Rule-based compliance and policy interpretation
Performs deep semantic analysis, classifying content into risk categories (compliant, potential violation, edge case, false positive trap). Doesn't just find keywords—understands context, intent, and implications.
Example: "Let's discuss this offline" in a product launch email is benign. The same phrase in financial reporting emails before quarter-end? Red flag for potential earnings manipulation.
Core Capabilities:
Detection Categories: Gift acceptance violations, insider trading indicators, conflicts of interest, data privacy breaches, harassment, financial reporting irregularities.
Specialty: Statistical and behavioral anomaly detection
Combines quantitative and qualitative approaches to identify unusual patterns.
Statistical Component:
Semantic Component:
Example: Employee receives three $249 gifts from same vendor (limit is $250). Statistical engine flags three near-threshold transactions in short timeframe. Semantic engine notices "just a small token" and "no need to report this" in emails. Together: clear threshold avoidance pattern.
Specialty: Synthesis, prioritization, and actionable reporting
Transforms technical findings into strategic intelligence tailored for different stakeholders.
Core Functions:
Stakeholder Adaptation:
Initialization → Load document, organizational context, user profile, compliance rules, baseline patterns
Sequential Processing → Agent 1 establishes baseline → Results inform Agent 2 focus → Agent 2 findings influence Agent 3 prioritization
Conditional Routing → High-risk findings trigger deeper analysis → Edge cases activate human review → Low-confidence assessments trigger additional agents
Error Recovery → Fallback to simpler analysis if advanced methods fail → Partial results if some agents error → Retry logic with exponential backoff
LLMs hallucinate—confidently stating plausible but fabricated regulations. You cannot have an AI inventing compliance rules.
Retrieval-Augmented Generation (RAG) solves this: Instead of asking the AI to recall regulations, provide the exact, current text of relevant rules for every analysis.
Core Principle: Don't ask "What are the rules about gifts?" Ask "Here are the exact gift acceptance rules [provides text]. Does this email violate them?"
Indexing (One-Time Setup):
Retrieval (Per Analysis):
Example: Analyzing email about conference sponsorship retrieves: gift acceptance policy, FCPA promotional expense guidance, industry regulations, recent clarifying memos, historical examples, threshold tables, approval workflows.
Construct sophisticated prompts with role definition, retrieved rules, document to analyze, violation/compliant examples, organizational context, analysis requirements, and structured output format.
Workflow: Construct prompt → Send to LLM → Parse structured response → Extract violations, confidence, evidence → Validate logical consistency → Return to Compliance Expert agent
Quality Assurance: Cross-reference across rules, verify evidence citations, flag low-confidence assessments, track false positives, continuous improvement through feedback.
Individual violations are data points. Real value comes from systemic patterns: Is Sales consistently pushing ethical boundaries at quarter-end? Are conflicts of interest more common in certain geographies? Are gift violations increasing month-over-month?
Key Insight: One gift violation is a training issue. A pattern of gift violations in Sales during Q4 every year is a systemic cultural problem requiring executive attention.
Data Preparation: Fetch vector representations → Combine textual embeddings with metadata → Apply dimensionality reduction → Normalize features
Clustering Process: Select algorithm (K-means, DBSCAN, hierarchical) → Determine optimal cluster count → Assign violations → Validate meaningfulness
Theme Extraction: Generate descriptive names → Identify representative examples → Analyze unique characteristics → Calculate trends over time
Example Discovered Themes:
Data Collection: Query violations for 30-90 days → Group by dimensions (time, department, type) → Calculate metrics → Establish historical baselines
Analysis Methods: Moving averages, trend lines, change point detection, seasonality analysis, baseline comparison
Alert Generation:
Example Insights:
Traditional keyword search is binary—a word appears or doesn't. Vector search understands meaning and context. It knows "accepting gratuities," "receiving gifts," and "taking kickbacks" are conceptually similar despite sharing no words.
Concept: Every document becomes a point in high-dimensional space (384-1,536 dimensions). Documents with similar meanings are geometrically near each other.
Convert query to vector → Calculate distances to indexed vectors → Retrieve k nearest neighbors → Apply metadata filters → Rank by relevance → Fetch full content → Format results
In compliance, time is risk. Real-time detection versus weeks-later discovery could mean preventing a regulatory disaster versus suffering one.
Trigger Mechanisms: Threshold-based (risk scores exceed limits), pattern-based (specific violation combinations), trend-based (concerning metric trends), manual escalation
Alert Composition: Severity classification, violation summary, evidence package, risk assessment, recommended actions, historical context, routing information
Distribution Channels:
Rules Engine: Role-based routing, time-based escalation, acknowledgment tracking, deduplication, aggregation
Streaming Architecture: Client opens persistent connection → System monitors database for events → Filter relevant updates → Push to connected clients → Handle disconnects gracefully
Update Types: New alerts, status changes, metric refreshes, analysis completion, system status
You need data to test but can't use real employee communications (privacy). Intelligent synthetic data generation solves this.
Template Foundation: Define realistic roles (executives, managers, analysts) → Create scenarios (vendor negotiations, project updates) → Establish conversation patterns → Set metadata distributions
LLM Generation: Provide detailed prompts → Generate natural email content → Inject realistic details → Vary writing styles → Include email artifacts
Violation Injection (15% of corpus):
Ground Truth Labeling: Binary violation flag, category/type, severity level, specific rule violated, evidence location, expected risk score range
Target Corpus: 3,000 emails (85% compliant, 15% violations) across 6 months, 10 departments, 50 synthetic employees
Normal Patterns: Payroll (regular cadence), vendor payments (monthly/quarterly), expense reports (employee-specific), capital expenditures (infrequent, large), revenue transactions
Anomaly Injection (10% of transactions):
Core Tables: emails, documents, analysis_results, alerts, themes, transactions, compliance_rules
Reference Tables: users, departments, vendors, rule_categories
Operational Tables: audit_logs, errors, performance_metrics, job_queue
Seed Data: 10 core compliance policies with full text, default configurations, user account templates
Data Lifecycle: Archive data >90 days old, compress archived data, delete temporary data, purge old cache
Database Optimization: Vacuum operations, analyze operations, reindex, partition management
Health Checks: Identify orphaned records, detect inconsistencies, verify integrity
Scheduled: Weekly cleanup, monthly archival, quarterly audits, annual updates
Metrics: Database (connections, query times, locks), Application (throughput, latency, errors), External services (API health), Resources (CPU, memory, disk, network)
Alert Thresholds:
Methods: Username/password (bcrypt hashing), SSO integration (SAML/OAuth), multi-factor authentication, API keys
Token-Based Sessions: Generate JWT tokens, include user claims, sign cryptographically, short expiration (8 hours) with refresh
Security: Password complexity, account lockout, rate limiting, brute force detection, session invalidation
Role-Based Access Control (RBAC):
Enforcement: Check permissions before operations, verify required roles, apply data filtering, log decisions, fail securely (deny by default)
Logged Events: Authentication, authorization decisions, data access, data modifications, configuration changes, administrative actions, API calls, system events
Log Structure: Timestamp, user ID, session ID, action, resource, IP address, request payload (sanitized), response status, execution duration, metadata
Properties: Immutable, complete, traceable, tamper-evident, retained for regulatory requirements (7 years)
Classification by Severity: Critical (system down), High (feature unavailable), Medium (performance degradation), Low (handled exceptions)
Classification by Type: Transient (network timeouts), Persistent (configuration errors), External (third-party failures), Internal (bugs)
Handling Process: Capture → Classify → Enrich context → Log → Alert if needed → Recover → Report appropriately
Retry Strategies:
Circuit Breaker Pattern: Track failure rate → Open circuit after threshold → Periodically test (half-open) → Close when recovered
The regulatory environment will only grow more complex. Data volumes will only increase. Traditional compliance approaches—sampling, periodic audits, reactive investigations—are becoming obsolete.
This architecture represents a new paradigm: continuous, intelligent, comprehensive compliance monitoring. Through orchestrated AI agents, semantic understanding, real-time alerting, and pattern discovery, organizations achieve the coverage and speed modern regulatory environments demand.
These principles apply regardless of technology choices—workflow platforms, traditional frameworks, or cloud-native serverless.
The question is no longer "Can we afford AI-powered compliance monitoring?" but "Can we afford not to?"
The frameworks are proven. The patterns are well-understood. The only variable is implementation commitment. For CFOs and compliance leaders looking to transform from reactive to proactive, from sampling to comprehensive coverage, from lag to real-time—the path forward is clear
Aryan R. is an MS candidate in Business Analytics & Information Management at Purdue University’s Daniels School of Business. He brings a B.Tech in AI & Data Science and hands-on experience across SQL, Python, visualization, and experimentation. Aryan is passionate about building data-driven products and communicating insights with clarity and precision. Outside academics, he’s a former national-level sprinter who brings the same discipline to his work.
Dr. Rohit Aggarwal is a professor, AI researcher and practitioner. His research focuses on two complementary themes: how AI can augment human decision-making by improving learning, skill development, and productivity, and how humans can augment AI by embedding tacit knowledge and contextual insight to make systems more transparent, explainable, and aligned with human preferences. He has done AI consulting for many startups, SMEs and public listed companies. He has helped many companies integrate AI-based workflow automations across functional units, and developed conversational AI interfaces that enable users to interact with systems through natural dialogue.